Back to the Central Hub
1.1 Compare and contrast the Open Systems Interconnection (OSI) model layers and encapsulation concepts.
OSI model - Open Systems Interconnection Reference Model
https://en.wikipedia.org/wiki/OSI_model
| OSI Model | Layer | Main Function | Protocols |
|---|---|---|---|
| Layer 7 | Application | File, Print, messaging, and other services | DNS, FTP, HTTP, POP3, SMTP, SNMP, DHCP |
| Layer 6 | Presentation | Syntax translation | |
| Layer 5 | Session | Dialog control, dialog separation | |
| Layer 4 | Transport | Data segmentation, packet acknowledgment, error detection and correction, flow control, port identification | TCP, UDP |
| Layer 3 | Network | Addressing, routing, error detection, protocol identification | IP, IPv4, IPv6, ICMP |
| Layer 2 | Data Link | Framing, media access control, protocol identification | IEEE 802.3 (Ethernet), IEEE 802.11 (Wi-Fi) |
| Layer 1 | Physical | Network interface hardware, binary signaling | Twisted pair, fiber-optic, Wi-Fi |
-
Originally published in 1984 by the international organization of standardization
-
A great mnemonic to remember the OSI model
- All People Seem To Need Data Processing
- Please Do Not Throw Sausage Pizza Away
-
While there have been other protocols over the years, LANs today nearly always run Ethernet or Wi-Fi at the physical and data link layers, Internet Protocol (IP) at the network layer, Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) at the transport layer, and a collection of Transmission Control Protocol/Internet Protocol (TCP/IP) protocols and services at the application layer.
-
The OSI model divides data communication into seven different layers
-
Layer 1 – Physical
- This layer is not about protocols
- Network Medium - The technology that carries signals from one computer to another
- copper-based cable
- fiber-optic cable
- radio transmissions
- connectors
- Network Interface - The connection between the computer and the network medium
- NIC’s (The port, not the job it does)
- The connection between the computer and the network medium, such as a cable connector or a radio transceiver
- Repeaters
- Hubs
- NIC’s (The port, not the job it does)
- Network Topology - The arrangement of the network medium
- Bus, Star, Hybrid, ring, mesh
- Network Installation - The guidelines for the installation of the network medium
- radio frequencies
- maximum cable lengths
- number of devices permitted
- proximity to other equipment
- Network Signalling - Specifies the nature of the signals
- electrical, optical, or radio,
- binary data over the network medium.
- Bits 1’s and 0’s
- bits are encoded into a suitable form for transmission such as voltage levels or waveforms
- voltage levels or waveforms are decoded back into bits at the destination
- Network Medium - The technology that carries signals from one computer to another
- If you have a layer 1 problem
- fix your cabling, punch downs, etc
- run loopback tests, test/replace cables, swap adapter cards
- This layer is not about protocols
-
Layer 2 – Data link
- Frame Format
- The data link layer protocol packages the data passed down to it from the network layer in a protocol data unit called a frame. A frame consists of a header and a footer generated by the data link layer protocol, with the network layer data as the payload in between.
- Addressing
- Every network interface adapter has a unique 6-byte identifier assigned to it by the manufacturer called a media access control (MAC) address. Data link layer frames use these addresses in their headers to identify the sender and recipient of each packet.
- Protocol Identification
- Data link layer headers include a code that indicates which network layer protocol generated the data in each packet. This enables the data link layer protocol on the receiving system to pass incoming traffic up to the correct network layer process.
- Error Detection
- The frame footer contains the result of a cyclical redundancy check (CRC) calculation performed on the frame’s data payload by the sending system. The receiving system performs the same calculation and, if the results do not match, discards the packet.
- MAC - Media Access Control
- When a LAN has devices connected to a shared network medium, the data link layer protocol uses a media access control mechanism to prevent two devices from transmitting simultaneously and causing a data collision.
- Physical Layer Specifications
- The data link layer protocol also includes specifications for the physical layer options associated with the protocol.
- Provides communication between directly connected devices
- Trouble Shooting
- If multiple frames contain errors in a switch’s log, the problem resides at the Data Link layer.
- Provides error handling for the OSI model’s physical layer
- Consists of 2 sublayers Media Access Control (MAC) and Logical Link Control (LLC) layers
- Media Access Control (MAC) Layer:
- The MAC layer is responsible for controlling how devices on a network gain access to the communication medium, such as a shared channel or a network segment.
- It defines the rules for addressing devices uniquely on the network through hardware addresses, commonly known as MAC addresses. These addresses are assigned to the network interface cards (NICs) of the devices and are used for the proper delivery of frames within a local network.
- MAC layer protocols determine how devices contend for and access the network medium, manage collisions, and handle frame addressing and synchronization.
- Logical Link Control (LLC) Layer:
- The LLC layer sits above the MAC layer and is responsible for establishing, maintaining, and terminating logical links between devices on the network.
- It provides flow control, error checking, and frame synchronization to ensure reliable data transfer between devices. Flow control mechanisms prevent fast senders from overwhelming slower receivers, while error checking helps in detecting and managing data transmission errors.
- The LLC layer helps in multiplexing multiple network layer protocols over the same physical medium, allowing different network protocols to coexist on the same network infrastructure.
- LLC acts as a common interface for network layer protocols, providing a standardized way for network layer protocols to access the services of the Data Link Layer.
- Media Access Control (MAC) Layer:
- sometimes referred to as the switching layer
- because switches make there forwarding decisions based on MAC Addresses
- also referred to as the Data Link Control (DLC) Layer
- there are a series of protocols that run as DLC protocols
- Ethernet
- Media Access Control (MAC) Address or Layer 2 address
- referred to as such because they link back to DLC Protocols
- Media Access Control (MAC) Address or Layer 2 address
- Ethernet
- there are a series of protocols that run as DLC protocols
- this is a layer that is foundational for the protocols that will be stacked on top of layer 2
- node to node data delivery
- Frames are created
- A physical address is added to the data being transmitted
- data is headed to a specific device on the network
- Transmission Control
- establishing and terminating links are established between nodes
- links are established before any data is transmitted
- links are terminated once the transmission completes
- media access management
- determines which node has control of the medium
- prevents 2 nodes transmitting at the same time
- determines which node has control of the medium
- flow control
- helps to prevent fast senders from overwhelming slow receivers
- error control
- damaged or lost frames are retransmitted
- access control
- specifies which node has control of a medium when a single channel is shared by many nodes
- establishing and terminating links are established between nodes
- Frame Format
-
Layer 3 – Network
- End-to-End Addressing The network layer protocol header contains the addresses of both the sending system and its final destination. Data link layer MAC addresses change for each leg of an internetwork journey, but network layer addresses always reflect a packet’s starting point and its final destination.
- Routing Routers are intermediate network layer devices that forward packets to other networks. Network layer protocols use routing tables to look up the addresses of other networks, so the router can forward packets to the correct destinations.
- Fragmentation Networks can have different frame size limits, based on their maximum transmission unit (MTU) values, so if a single frame is too large to transmit over another network, the network layer protocol splits it into smaller fragments and transmits each fragment in a separate frame. The network layer protocol reassembles the fragments when they reach their final destination.
- Protocol Identification Just as a data link layer protocol header contains a code to identify the network layer protocol that generated the data in the packet, the network layer protocol contains a code identifying the transport layer protocol that generated the data.
- Components associated with the Network layer
- IP Address
- Subnet mask
- Default Gateway
- Routing Information
- Routers function on the Network layer
- This layer is responsible for forwarding packets to specific routes on the network
- This layer analyses the packets received and determines if it has reached its destination and then passes it to the Transport layer.
- If it is not the final destination, it will pass it to the Data link layer until it reaches its final destination.
- The Network layer is also responsible for updating routing tables.
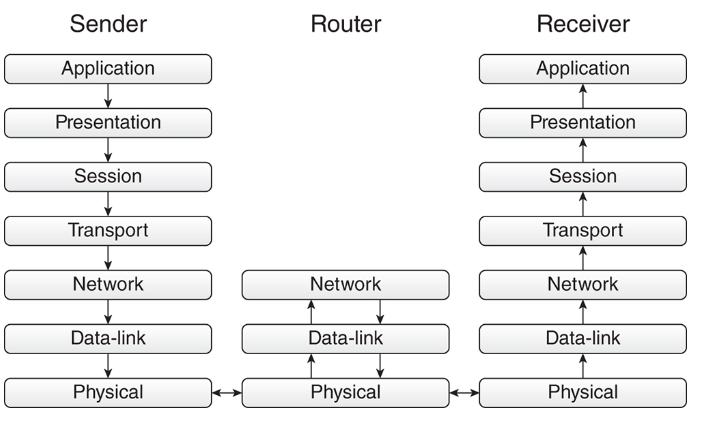
- Protocols such as IPX, NetBEUI, and IP operate at the Network layer.
-
Layer 4 – Transport
- The Transport layer’s function is to deliver data across network connections
- The most commonly used protocols are TCP (Transmission Control Protocol) Port numbers and UDP (User Datagram Protocol) port numbers.
- Different protocols will have different functionalities when transporting data across the network. For example, error checking is done using the TCP protocol.
- provides connection-oriented communications. Protocols such as TCP operate at the Transport layer.
-
Layer 5 – Session
- The OSI model’s Session layer manages the flow and sequence of different network connections.
- This ensures the possibility for dynamic concurrent connections.
- The control layer, tunnelling information or setting up communication from one device to another
- control and tunnelling protocols
- SPDU - Session Protocol Data Unit
- The OSI model’s Session layer manages the flow and sequence of different network connections.
-
Layer 6 – Presentation
- the Presentation layer handles the processing and converting of the data, for example, encryption and decryption, to facilitate the support for the Application layer.
- SSL - Secure Sockets Layer
- TLS - Transport Layer Security
- PPDU - Presentation Protocol Data Unit
- the Presentation layer handles the processing and converting of the data, for example, encryption and decryption, to facilitate the support for the Application layer.
-
Layer 7 – Application
- the Application layer provides network services to applications.
- These services include protocols that integrate into the application; for example, the HTTP protocol is used to deliver data to a web browser to display a user’s web page.
- APDU - Application Protocol Data Unit
- the Application layer provides network services to applications.
- The OSI Model is primarily used for teaching purposes and has been superseded by the TCP/IP model.
-
-
Data encapsulation and decapsulation within the OSI model context
- Encapsulation in the OSI model involves wrapping data with protocol information at each layer, from application down to physical, before transmitting it across the network. Decapsulation is the reverse process on the receiving end, where each layer removes its corresponding headers or trailers.
-
Ethernet header
- The Ethernet header is added at the Data Link Layer (Layer 2) and contains essential information like source and destination MAC addresses, which enables devices to route frames within the same local network or subnet.
-
Internet Protocol (IP) header
- Added at the Network Layer (Layer 3), the IP header contains source and destination IP addresses, allowing data packets to be routed across networks to reach their designated endpoints.
-
Transmission Control Protocol (TCP)/User Datagram Protocol (UDP) headers
- These headers are part of the Transport Layer (Layer 4). TCP provides reliable, connection-oriented transmission with sequence and acknowledgment fields, while UDP provides a faster, connectionless option without reliability checks.
-
TCP flags
- TCP flags, included in the TCP header, help manage the flow of data. Flags like SYN, ACK, FIN, and RST control connection establishment, acknowledgment, teardown, and reset processes within the TCP protocol.
-
Payload
- The payload is the actual data being transported, which the application at Layer 7 wants to send or receive. It remains intact as headers are added or removed at each OSI layer during encapsulation and decapsulation.
-
Maximum transmission unit (MTU)
- MTU defines the largest size of a frame or packet that can be transmitted across the network at one time, determined by the physical network layer. Exceeding the MTU causes fragmentation, handled at Layer 3.
-
Maximum segment size (MSS)
- MSS is a TCP-level parameter that specifies the largest amount of data the TCP layer can receive in a single segment, excluding TCP headers. MSS helps avoid IP fragmentation, optimizing transmission within the MTU limits.
-
- Encapsulation in the OSI model involves wrapping data with protocol information at each layer, from application down to physical, before transmitting it across the network. Decapsulation is the reverse process on the receiving end, where each layer removes its corresponding headers or trailers.
Links to Videos and Additional reading
Professor Messer 1.1 – The OSI Model
Back to the Central Hub